Refraction Networking
Internet freedom in the network’s core
What is refraction networking?
Most of today’s censorship circumvention tools use the same fundamental approach: they encrypt the user’s traffic to make it look innocuous, and channel it to a proxy server located outside the censored network. This leads to a fundamental problem: Once the censor discovers the proxy server, the proxy itself becomes just another site to block. If users can find the proxy servers, the censors can too.
In this race to find and use—or find and block—proxy servers, censoring governments enjoy natural, growing advantages over censored users. For example, they can examine all data flowing across their borders in search of disfavored activity. Strategies that rely on friendly servers are failing against increasingly sophisticated state-level censors who can see and control a country’s entire network.
Refraction networking
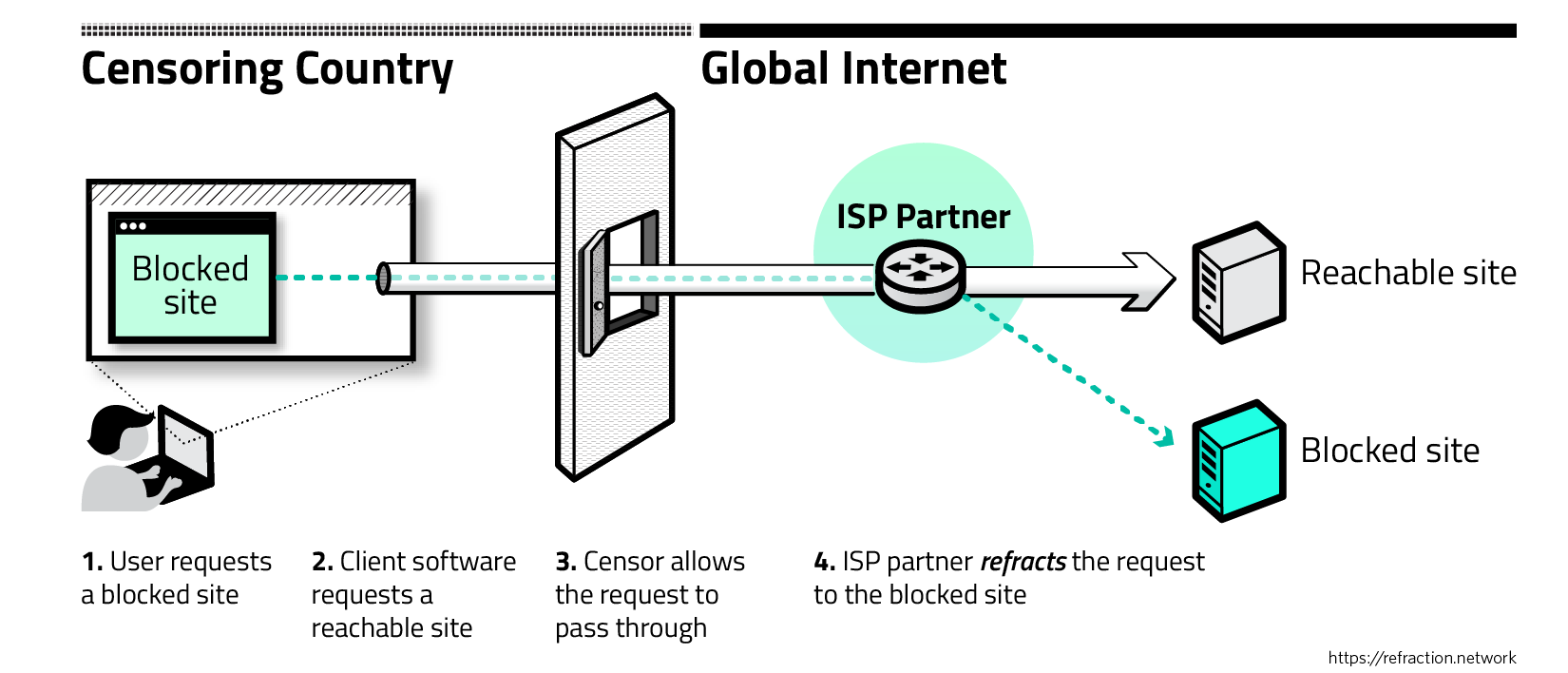
What work is happening now?
Refraction networking was independently invented in 2011 by three engineering teams. Five protocols exist: Telex and TapDance at the University of Michigan, Cirripede at the University of Illinois, and Curveball and Rebound at Raytheon BBN Technologies. These designs share the same basic premise but represent a range of design choices and technical tradeoffs.
Today, researchers from Michigan, Illinois, and the University of Colorado have formed a coalition to make refraction networking a widely deployed and powerful tool for Internet freedom, with support from the U.S. State Department's Bureau of Democracy, Human Rights, and Labor. Since 2019, the coalition has been operating a real-world production deployment that provides refraction networking service to more than a million users globally.
What research has been published?
The papers are:
-
Operational Deployment
- Running Refraction Networking for Real
Benjamin VanderSloot, Sergey Frolov, Jack Wampler, Sze Chuen Tan, Irv Simpson, Michalis Kallitsis, J. Alex Halderman, Nikita Borisov, and Eric Wustrow
Proc. 20th Privacy Enhancing Technologies Symposium (PETS ’20), July 2020. - An ISP-Scale Deployment of TapDance
Sergey Frolov, Fred Douglas, Will Scott, Allison McDonald, Benjamin VanderSloot, Rod Hynes, Adam Kruger, Michalis Kallitsis, David G. Robinson, Nikita Borisov, J. Alex Halderman, and Eric Wustrow
7th USENIX Workshop on Free and Open Communications on the Internet (FOCI ’17), August 2017. - TapDance source code on Github.
- Running Refraction Networking for Real
- Announcement on Medium.
- Conjure: Summoning Proxies from Unused Address Space
Sergey Frolov, Jack Wampler, Sze Chuen Tan, J. Alex Halderman, Nikita Borisov, and Eric Wustrow
26th ACM Conference on Computer and Communications Security (CCS ’19), November 2019.
- TapDance: End-to-Middle Anticensorship without Flow Blocking
Eric Wustrow, Colleen M. Swanson, and J. Alex Halderman
23rd USENIX Security Symposium, August 2014.
- Telex: Anticensorship in the Network Infrastructure
Eric Wustrow, Scott Wolchok, Ian Goldberg and J. Alex Halderman
20th USENIX Security Symposium, August 2011. - The Telex web site, with clear visual explanations of the system.
- Rebound: Decoy Routing on Asymmetric Routes Via Error Messages
Daniel Ellard, Alden Jackson, Christine Jones, Victoria Manfredi, W. Timothy Strayer, Bishal Thapa, and Megan Van Welie
40th IEEE Conference on Local Computer Networks (LCN ’15), 2015.
- Decoy Routing: Toward Unblockable Internet Communication
Josh Karlin, Daniel Ellard, Alden W. Jackson, Chistine E. Jones, Greg Lauer, David P. Mankins, and W. Timothy Strayer
1st USENIX Workshop on Free and Open Communications on the Internet (FOCI ’11), August 2011. - Curveball web site with more information and source code.
- Cirripede: Circumvention Infrastructure using Router Redirection with Plausible Deniability
Amir Houmansadr, Giang T. K. Nguyen, Matthew Ceasar and Nikita Borisov
18th ACM Conference on Computer and Communications Security (CCS ’11), October 2011.
Beyond the work of our coalition, several other research papers directly address issues connected with refraction networking:
-
Slitheen: Perfectly Imitated Decoy Routing through Traffic Replacement (CCS '16)
Optimizing the Placement of Implicit Proxies (Princeton CS Technical report)
Routing Around Decoys (CCS ‘12)
No Direction Home: The True Cost of Routing Around Decoys (NDSS ‘14)
How can I get involved or find out more?
The refraction networking coalition is working to partner with network operators. If you’d like to find out more or help support our efforts, please contact us at team@refraction.network.